Ransomware is now a common (and often recurring) threat to modern organisations and regardless of size or sector, businesses are now being forced to move from an “if it happens” to a “when it happens” mindset.
Entering 2024, for the fourth year in row Cyber-attacks were the leading cause of ‘impactful outages’ with 3 out of 4 organisations suffering at least one Ransomware attack in the preceding 12 months.
As a follow up to the webinar “Breaking the Ransomware Cycle”, hosted by virtualDCS and Veeam, we’re releasing a series of blogs with the goal of helping readers to:
- Gain a clear understanding of the Ransomware landscape.
- Learn how to formulate a plan to ensure you’re best equipped to limit the impact of Ransomware.
- Discover what you need to consider to recover and evolve from a Ransomware attack
To view the accompanying webinar, click here.
Part 1: Understanding the Ransomware landscape: Originally led by Nick Furnell, Senior Cloud SE at Veeam.
There’s no denying that Ransomware is now part of our everyday lives. Here are a few Ransomware statistics to help generate a picture:
- More than 75% of organisations suffered a Ransomware attack in some form during 2023.
- On average, it takes businesses three weeks to recover from each attack.
- Bitcoin currently accounts for approximately 98% of Ransomware payments.
- As the Ransomware footprint has increased, so has the price of the ransom itself and in some extreme cases attackers demanded victims pay as much as $80 million.
- The cost of Cyber-attacks could reach $10.5 trillion worldwide by 2025.
- Where a business pays the ransom, the payment is roughly 15% of the total cost to the business. With system restoration, legal fees, monitoring costs and overall business disruption on top.
Understanding Cyberattacks
The first step in developing a comprehensive Ransomware recovery strategy is to acknowledge how it attacks an organisation. How does Ransomware work? As a simple description, Ransomware works by infecting a device or network, with the goal of encrypting the files and data stored within them.
How is Ransomware infect a system? Ransomware can infiltrate a network in a number of ways, but the most reported attack vectors include:
- Exploitable vulnerabilities
- Brute-force credential attacks
- Social engineering and phishing attacks
- Use of previously compromised credentials
- Abuse of trust and insider threats
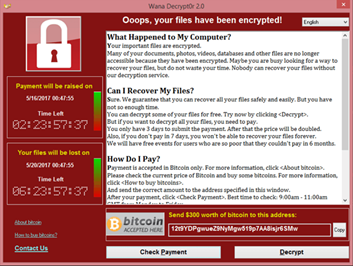
Once infected the Malware crawls through the network, encrypting any data it finds, before it then displays a ransom note demanding payment.
This payment is usually in the form of Cryptocurrency, in return for the decryption key that unlocks the files. If the ransom isn’t paid by a certain deadline, the attackers may threaten to permanently delete the data or even leak it publicly.
Even if an organisation pays the ransom, statistics show that only a third of those who pay actually get their data back, and there is still the long-lasting threat that copies of the information will be made public. This is why organisations are 2.5 times more likely to pay a ransom in cases where data has been exfiltrated on top of the encryption.
To help build out the picture, let’s explore a typical Ransomware cyber-attack timeline, as presented by Veeam in the webinar.
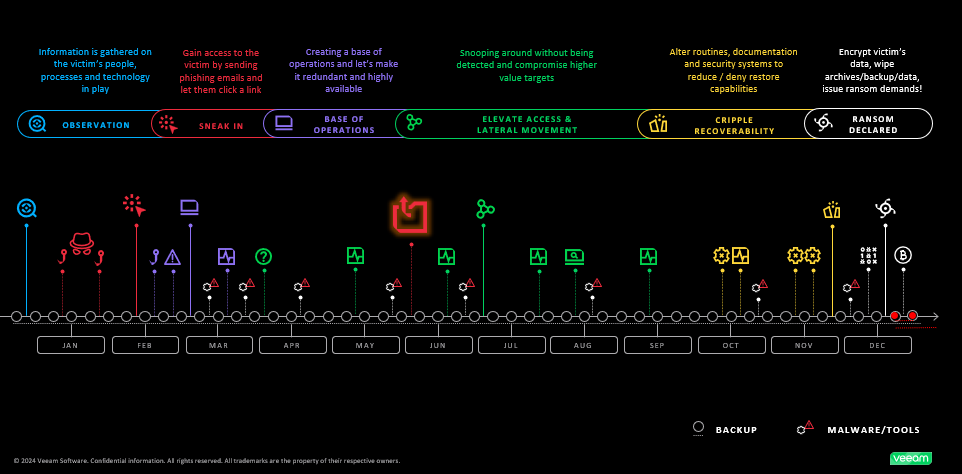
Phase 1: Observation
Attackers will likely observe your behaviour, often using social media to look for a weak link in the chain and one common entry point is via new employees as they establish themselves in a new role.
Phase 2: Infiltration
Many attacks begin with a seemingly harmless link that turns out to be Phishing. How likely is a new employee to ignore an email and link with instructions from senior management? In 2022, 69% of Ransomware attacks on businesses started with an email and a simple click creates a foothold for attackers.
Phase 3: Establishing a Base
A single compromised account can provide attackers with a springboard to launch further attacks. They’ll then seek to establish a foothold within your infrastructure, branching out and gathering as much information as possible.
Phase 4: Expanding Control
Attackers will then attempt to move laterally through the network, seeking valuable data and elevated access. Imagine a skilled thief strategically manoeuvring through your IT infrastructure. This is where data exploitation and exfiltration can happen and it can be much more harmful and impactful for organisations as this data may have higher long-term value.
Phase 5: Prevent recoverability
Neutralising backups is a top priority for attackers, ensuring that the organisation loses access to its recovery options. 93% of Cyberattacks now also target backup repositories and centralised backup solutions make it much easier to access crucial data without navigating production systems. We’ll discuss alternatives to centralised backups in part two of this series.
Phase 6: Declaring the ransom
Hackers automate tasks by installing remote access tools like AD Find or Global Strike Beacon, sending signals every few minutes to ensure the infrastructure remains accessible to them. They may not know that the ransom message has been deployed straight away, so its important that IT teams stay calm and avoid contacting the hackers to keep this under wraps for as long as possible. We’ll also be discussing how to respond to a Ransomware attack in part three of the series.
Expedited attacks and Ransomware kits
Through “Ransomware as a Service” hackers also now have access to pre-packaged Ransomware tools and strains, along with sophisticated Ransomware affiliate programs, which offer commission to individuals that distribute Ransomware. These commission rates range from 5% to 40% of the total ransom collected.
With this in mind, it’s not uncommon to see hackers hand over Ransomware attacks to other groups through each stage of the timeline.
Now we’ve got a picture of the Ransomware landscape and how it infiltrates an environment, we now need to explore how to form a Ransomware recovery plan, which we’ll cover in the next blog.
If you can’t wait to read the next part, you can view the full webinar on-demand, here.
